GEICO can save you 20%,
IT Security can save you 100% of your business.

Smart business people are continuously looking for new ways to cut costs and minimize risk. Getting a 20% discount on your car insurance is a good start but it’s a sad state of affairs if you’re:
- Financial Statements
- Banking Information
- Business Plans
- Product Pricing & Service Rates
- Customer Data
- Engineering Drawings, Photos & Prototypes
- Legal Matters
- Personal Items
are exposed to both internal and external threats. Everything in your computer, network, router, printer and wireless device exposes you and your company to a major, catastrophic event. You may not know about it for months or you may never find out unless you look and have an objective, Outside Source do the investigation.
Spending money on Cyber Security may have drastically varying results. The lowest price doesn’t give you the best value either. History shows us that most organizations that install standard issue, off of the shelf technology end up begging for assistance because they are living with a false sense of security.
These people hold confidential information in their offices and they employ Commercial off the Shelf (COTS) products which are manufactured in potentially rogue nations. Simply, look at the label on your Laptop, Modem, Router, Printer, etc. Where is it manufactured? Is it possible that you are using technology with a preexisting virus or a built in back door? How would you know?
IT Security solves problems, we have many clients which were hounded by the Hackers, so much so that Email was Unusable (full of Spam and Viruses), their Internet Connections were always full, and they were completely unstable and unusable. Imagine if you will that you are a vendor to another company, perhaps you are working with Target or another organization. The last thing that your business needs is to be is identified as the reason for a Breach in security, this could be the end of your business.
What’s the actual cost of vulnerabilities discovered in your network?
More than a third of organizations that experienced a data breach in 2016 reported substantial customer, opportunity and revenue loss of more than 20 percent. Is your organization prepared?
The Business clients which we worked with all tried new products from many different vendors. They tried new Firewalls, and new Internet Service Providers, New Mail Systems, and they even had their IT Departments try to plug the leaks with new virus scanners. None of these actions solved their problems. The problem here is that they are not Cyber security professionals, and they were trying to apply a band aid to the problem.
IT Security already had a solution which protected its systems, including the Email Filtering Service we call Spam Zapper. The difference with our solution and others is a trade secret, but suffice it to say that we daily defend our systems from more than 50,000 scans and attacks. No other Email solution we have identified actually includes an Advance Cyber Defense Firewall to protect their email, and the rest of the organization.
Our solution, called ‘Active Defense’ automatically detects and defends against malicious connections, Blocks unwanted attacks, and protects the server, so that it is able to be used for its intended purpose (Email, Web Services, DNS …) and not as an attack point for the Hackers. The longer the server can run, the more time you have to run your business, safely and securely.
The image below is a screenshot of a report showing the server was last rebooted 522 days ago (see yellow highlight). This is not unique, we see this all the time when servers are using our ‘Active Defense’.
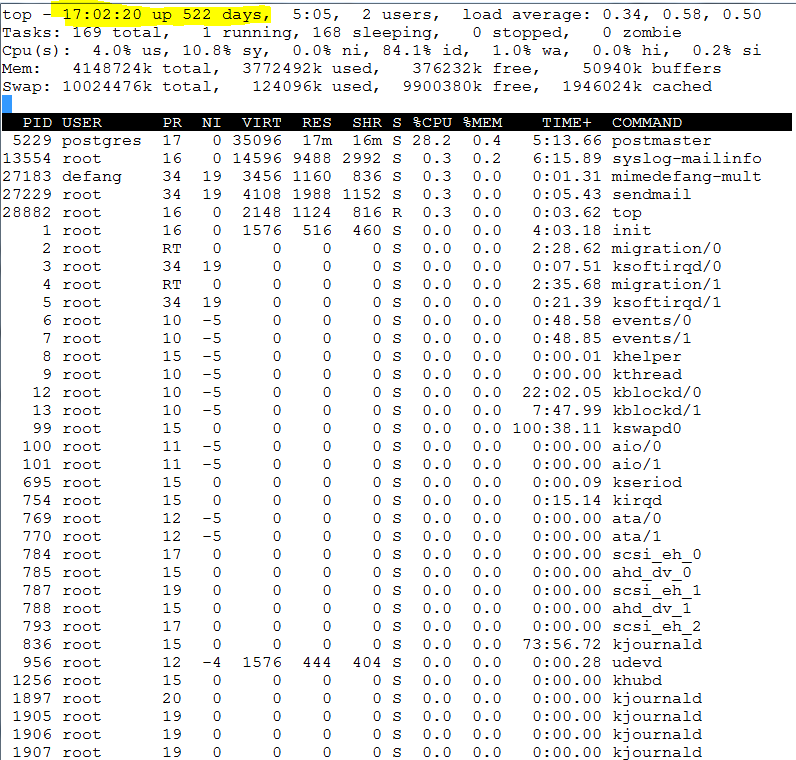
Figure 1- Screenshot from a server running for 522 days.
IT Security is different, we are Certified Cyber Security Consultants and have been developing solutions for Business and Government systems since 1987. We use a blend of proprietary solutions and commercially available systems. We are fundamentally vendor agnostic and we use the solutions that we recommend (the image above reflects our experience). Here are a few of the solutions we have readily available:
- Active Defense – Protects our servers online, and internally. When this article was written, two servers were running for more than 500 days (one for 503 days, and one was at 522 days with NO RESTARTS). Are your systems secure enough to run this long without incident?
- Spam Zapper – Our Spam Zapper Email Filtering service is the first to employ its own Firewall wrapped into the Email Service directly, eliminating the Spammers, and protecting your Email systems from the Hackers as well. It will provide you with a SPAM Score on questionable emails. Let us eliminate your Spam, Malware and Ransomware.
- Code Dx – Code Dx is a solution for getting Security and Application Development Teams to talk together, and enable them to design security into the applications and develop, safe, secure software at DevOps Speed. This strategy is vastly superior to attempting to retrofit cyber security measures after your application has been built.
- Security Assessments – Our Experienced professionals have the ability to provide network assessments, software analysis (Static and Dynamic), as well as Strategic Enterprise Risk assessments.
- Training – We offer everything from Basic Cyber Awareness training and Compliance Training (NIST, HIPAA, etc.) to Advanced Secure Software Development Techniques. Often our Training is customized to your organizations specific needs which includes training for the Tools and Software that we install.
Yes we can offer additional resources, but the best approach is not to compete for your business based on price but to provide you with a plan based on a fully developed understanding your situation, the mission you are supporting and the threats that you are facing now and in the future. The value of a secure environment is incalculable. IT Security can literally save 100% of your business.
The point is that at IT Security we understand what the Hackers are seeking and how they operate. Are you playing into their hands by using tools and preventive measures that are very common and readily available to the Hackers, some of these tools may already have built-in back doors?
Our professionals can determine the level of security that you have versus the level of security that is necessary. We assure you that as your Teaming Partner we can keep you free of breaches and keep your name out of the nightly news. In addition we can keep the Hackers and the Government out of your wallet.
Security efforts employed before a breach are 10 to 100 times less expensive than the cost of remediation after a breach occurs. If you are waiting for an event such as a breach, what will it cost you then? How do you plan to get your data back?
So GEICO will save you 20%, but is that what are you concerned about? Saving 20% on car insurance or saving 100% of your business?
Forget about saving 20%, let’s save 100% of your business by scheduling your free Security Assessment now.
![]()
IT Security is a HUBZone Certified, Service Disabled Veteran owned business (SDVOSB), expert security consulting company with more than 40 years of professional experience in protecting organization’s most valuable information. We have successfully protected clients ranging from small to Global businesses, financial institutions, federal agencies, and all five branches of the military.
In short, IT Security is a Full Service IT Security Consulting Firm. We have the Credentials, the Tools and the Experience to develop and implement a comprehensive Strategy to keep your information yours. We offer another set of eyes, a very objective set of eyes that have seen just about everything over the years.
IT Security, Inc. executes penetration testing using our exclusive Assessment and Auditing programs that isolate the same vulnerabilities a hacker will exploit on your network or servers. We remove those vulnerabilities with our custom solutions that create and maintain significantly stronger and safer IT environments for your critical information. We keep the hackers out, the production environments secure and compliance cleanup costs to a minimum. Most businesses are completely unaware of their system’s blind spots regarding the cyber threat landscape; stay ahead of the cyber security curve and allow us to safeguard your production environment.
Click here to schedule your free initial security assessment, the savings you receive on this call will make a difference in your business.
IT Security, Inc. • Info@IT-Security-inc.com • Phone: 412-515-3010





